Social networks like Facebook, Twitter, LinkedIn and MySpace have added an integrated level of communication that we have not seen before now. Along with the convenience and ease of use comes responsibility to use the technology appropriately.

It seems that with the introduction of new technologies, the majority of people fail to transition what they’ve learned from earlier technologies or direct interactions to the new medium. To illustrate my point, if someone walked up to you while you were waiting for a bus and said they were from your bank and needed to verify your ID, pin# and CC #’s, would you comply? What if we step it up a notch and the person that approaches you is dressed in proper uniform with a name tag and has a clipboard with “their” logo and your name at the top of the page and asks you to fill it out? It seems compelling, but you weren’t going to the bank, you weren’t thinking about the bank, and you wouldn’t expect anyone around you to even know where you banked. Something seems fishy, right? Scammers, phishers and cons can create very compelling authentic sounding emails with proper graphics and logos that ask you to log in to your bank account to update or confirm your information to reinstate your account. I can’t conceive of a sane person that would comply with the above real-world example, yet thousands of people unfamiliar with technology have complied with the exact same request through email!
Within “phishing” emails are usually links that direct you to a fake web site where they ask you to log in and type in further information that may be used to help them steal your identity. Who knows how far they went to create this site, and maybe it stores the username and password and gives you an error message (incorrect password) prompting you to try again… this only helps them out because now you’re typing it in more carefully a second (or third?) time. Perhaps they spent more time developing this page and have a further request behind the login page that asks for more information. This is not the usual approach, as they usually take the “let’s see what sticks” approach.
I can speculate all day about what these attacks will do and how they will be designed, but I feel comfortable saying that this will not end any time soon and will become increasingly sophisticated. As a matter of fact, I expect the most popular online activity to be exploited more heavily this year: social media websites. What if you were invited to a Facebook fan page for your bank that asked you to authorize the app on the page, then the page informed you that you’d be entered into a drawing for a $1,000 Visa gift card? All you have to do is confirm your bank account number and the attached debit card information… would you do it? Is there any way to know that the information you typed in was actually going to the bank you are being compelled to believe? No, and again I say, no!
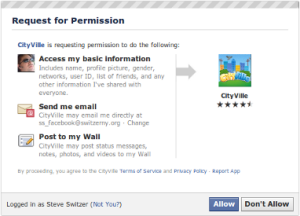
Facebook has already seen its fair share of phishing and information gathering attacks, and most of them involve page “Likes” or apps that require you to “Allow” them access before you use them. Good examples of legitimate apps that request this are Farmville, Cafe World, Mafia Wars, etc. Zynga (the publisher of those games) is reputable but other apps (a quiz perhaps?) could be made by anyone. The quizzes gather information about you, and are given permission to write to your wall. Sometimes the permission requested allows for wall updates even when you’re not on-line!
What about the wall posts that say things like, “Wow did you see what pthis father did to his daughter?” Things such as these usually require you to “Like” them before you’re allowed to see the information they promise. The act of liking creates a wall post telling everyone that you like what you saw and prompts others to view it. This method of spreading is known as “viral” not because it’s a virus, but because is spreads from profile to profile easily and quickly through the actions of the profile owner(s). These may not pose much risk directly and thus seems innocent, but could easily be combined with other methods and lure unsuspecting users. Besides, it’s the principle of the thing that tells me to refuse to “Like” something before I even know what it is!
Would you fall victim to an attack that involved both email and social networking? Just this past December, scammers were sending SPAM emails to random people, telling them to verify their Facebook account or it will be deleted. This email directs people to an app on facebook.com (so it looks legit, since it’s on the real Facebook site) and this app gathers information that people type in, as well as directly from the user’s profile! You can read about it here: http://timesofindia.indiatimes.com/city/pune/Facebook-site-under-fresh-phishing-attack/articleshow/7026093.cms This is not the first kind of app that will do this, nor will it be the last. Be wary!
The message I’m trying to convey is to be aware of the risks with apps that ask you for permission to access your account and personal information, as they are only getting more prevalent on social networks.
Before you allow an app to access your account, or you “Like” something on Facebook, ask yourself these questions:
Social exploits are becoming more and more clever and will continue to do so. Be ready. Be smart. Interact safely.